Last week, Gartner® released a new emerging technology report on preemptive security solutions. The report, titled Emerging Tech: Build Preemptive Security Solutions to Improve Threat Detection (Part 2), in which ZEST was named a sample vendor for preemptive exposure management, explores how preemptive security enables organizations to strengthen their defenses against emerging threats.
Why the Shift to Preemptive?
Attackers are increasingly leveraging AI to automate attack techniques, enabling them to gain initial access and execute critical attack stages at a faster speed than ever before. Attackers are innovating and operating at such a rapid pace that a reactive approach – especially when it comes to managing risk exposure – is no longer sufficient. A preemptive approach is now critical – one that incorporates the latest advancements in AI to increase the speed and accuracy at which defenders can proactively prevent or disrupt attacks before they can launch or advance.
The concept of preemptive security extends beyond exposure management, applying across multiple areas including:
- Preemptive exposure management
- Advanced obfuscation
- Threat intelligence
- Advanced cyber deception
- Automated moving target defense
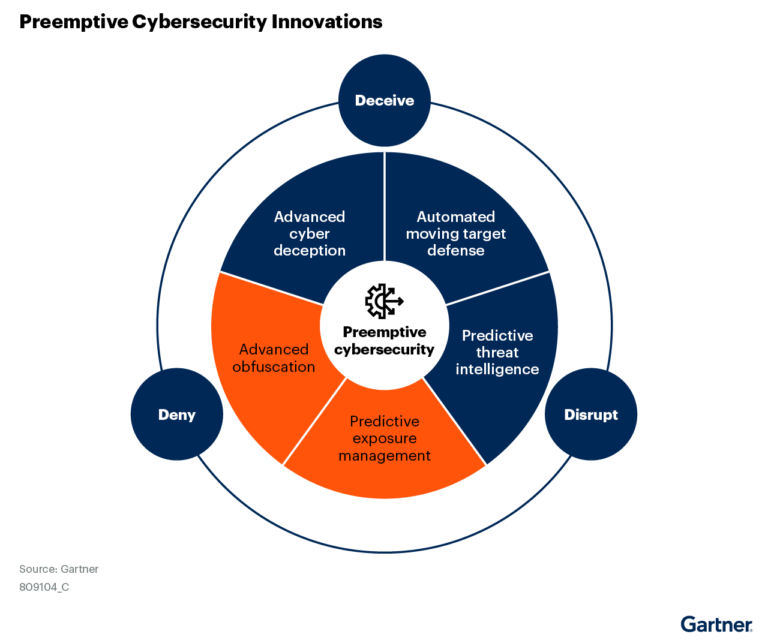
Preemptive Exposure Management Explained
As defined by Gartner®, preemptive exposure management “is not a separate technology category; it is a progressive approach to executing exposure management”.
While exposure management is inherently proactive, with the goal of reducing exposure by addressing vulnerabilities, misconfigurations, and other risks before attackers can exploit them, traditional approaches have fallen short – especially in complex cloud environments. While security teams are highly effective at identifying risks, significant gaps remain in how these issues are resolved, as evidenced by significant remediation delays. Preemptive exposure management aims to address these critical gaps by streamlining risk management as an end-to-end process using innovations such as AI and intelligent simulation to enable faster and more precise remediation and mitigation actions.
A preemptive exposure management approach/solution enables security teams to:
- Prevent attackers from initiating attacks e.g. exploiting open vulnerabilities, misconfigurations and other risks
- Disrupt ongoing attacks at various stages e.g., reconnaissance, lateral movement, privilege escalation, data encryption, etc.
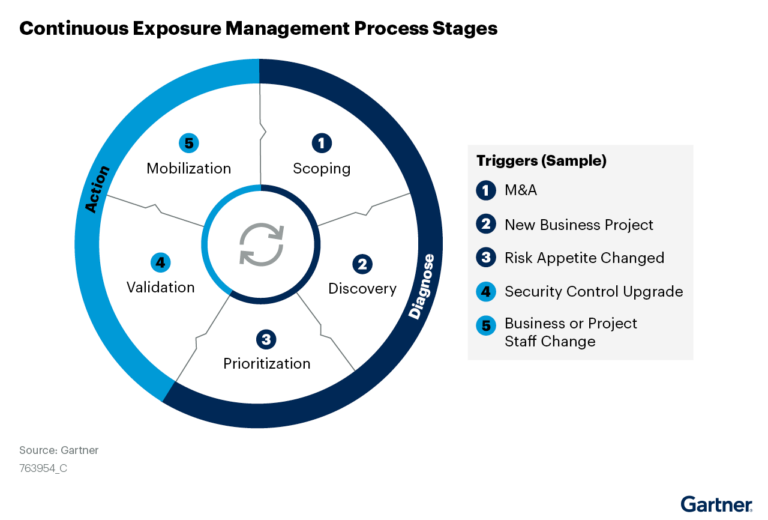
How Preemptive Exposure Management Aligns to Continuous Threat Exposure Management (CTEM)
As noted in the report, to truly move from a proactive to preemptive approach for exposure management, critical process stages of CTEM must be addressed, from discovery to mobilization.
- Discovery: Identification of risks including vulnerabilities, misconfigured assets, posture issues, etc.
- Prioritization: Prioritization of findings based on risk, exploitability, reachability, business criticality, availability of mitigating controls, impact on the risk backlog and remediation effort.
- Validation: Validation of threats, their impact, and remediation efficacy.
- Mobilization: Execution of precise remediation or mitigation actions.
The Link Between Exposure Management and Threat Detection and Response
To enhance detection and response, integrating preemptive capabilities, including preemptive exposure management is key. A preemptive exposure management approach not only bridges the gap between identifying risk findings and applying solutions – reducing the time and complexity of remediation and mitigation efforts. It also ensures that the solutions you implement today also prevent future and recurring risks. For example, a preemptive approach enables organizations to implement a feedback loop to continuously refine and enhance detection mechanisms.
How ZEST Delivers Preemptive Exposure Management
ZEST streamlines end-to-end remediation operations, leveraging Agentic AI to drastically reduce the complexity and time it takes to resolve cloud security, AppSec issues and other risks. As an AI agnostic solution, the platform employs various LLMs and AI Agents that excel in specific remediation tasks, extending and enhancing security teams. The platform offers a unified view of prioritized findings including vulnerabilities, AppSec issues, misconfigurations, and software supply chain risks, and delivers fully guided remediation and mitigation.
Core Capabilities:
- AI-generated resolutions: AI agents examine infinite options for resolution, mapping open findings to the best possible solution based on available fixes, remediations, and mitigations.
- Intelligent simulation: Simulates the implementation of patches, package updates, IaC and code fixes to determine which resolution paths resolve the most findings at once.
- Exposure validation: Validates risk exposure and that remediation and mitigation actions were effective to close the remediation loop.
- Seamless integration: Integration with the security stack including CNAPP, CWPP, CSPM, AppSec solutions, vulnerability management platforms, DevOps systems, and ticketing and communication and ticketing systems.
Ready to see ZEST in action?
To see ZEST’s unique approach to preemptive exposure management, contact our team to schedule a demo.