Introduction
AWS Organizations is a service that enables centralized governance and management of multiple AWS accounts. It allows for consolidated billing, policy-based control, and automated account creation. A key feature of AWS Organizations is the Delegated Administrator, which allows you to delegate administrative responsibilities to specific accounts without relying on the management account for all tasks.
This blog explores the security pros and cons of using Delegated Administrator in AWS Organizations, its impact on Security Control Policies (SCPs), and best practices for implementation.
Understanding AWS Organizations and Delegated Administrator
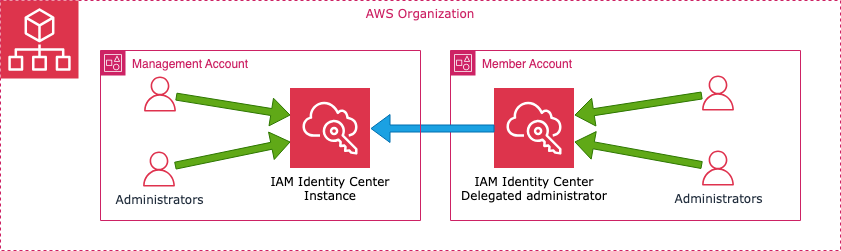
AWS Organizations provides a hierarchical structure for managing AWS accounts. The management account is the primary control point, but it is not recommended for daily administrative tasks due to security and operational risks. Instead, AWS allows you to delegate administrative control of specific services to another member account, reducing reliance on the management account.
How Delegated Administrator Works:
- The management account grants another AWS account within the organization the ability to manage specific AWS services.
- The delegated account can perform administrative actions for a service (e.g., AWS Security Hub, AWS Config, GuardDuty) without requiring access to the management account.
- Only certain AWS services support Delegated Administrator roles (e.g., AWS Security Hub, AWS Config, AWS Organizations itself).
Security Pros of Using Delegated Administrator
- Reduces Reliance on the Management Account
- The management account is the most privileged account in AWS Organizations. By using a delegated administrator, you minimize direct access and exposure to potential threats.
- Enhances Least Privilege Access Control
- Instead of granting broad permissions to all users in the management account, you can assign granular permissions in the delegated account.
- Improved Compliance and Auditability
- Delegated accounts can have dedicated logging and monitoring, improving visibility into security operations and reducing risks associated with overuse of the management account.
- Separation of Duties
- Allows security, billing, or compliance teams to have their own administrative roles without needing direct access to the management account.
- Enforces SCPs Consistently
- SCPs (Service Control Policies) apply uniformly across delegated accounts and member accounts that are not management, ensuring that governance rules are maintained regardless of where administration occurs.
Security Cons of Using Delegated Administrator
- Potential Misconfiguration Risks
- Delegating administration to an account without properly scoping permissions can lead to excessive privileges or misconfigurations.
- Limited Service Support
- Not all AWS services allow delegated administrators. If a service does not support delegation, all administrative actions must still be performed via the management account.
- Cross-Account Trust Risks
- Delegated administration creates cross-account trust relationships. If the delegated account is compromised, an attacker could gain elevated privileges within AWS Organizations.
- SCP Complexity
- SCPs apply at the organization level, and without proper planning, they could block necessary actions for a delegated administrator, causing disruptions.
- Loss of Centralized Visibility
- If not properly configured with AWS CloudTrail and AWS Config, security teams may lose visibility into delegated administrative actions.
Impact on SCPs and Governance
When using Delegated Administrator, Service Control Policies (SCPs) continue to apply across the entire AWS Organization. Here are some key impacts:
- SCPs Apply to Delegated Accounts: Even though a delegated administrator has permissions, it cannot override SCP restrictions set at the root or organizational unit (OU) level.
- Blocking Certain Administrative Actions: If an SCP blocks an API action, the delegated administrator account cannot bypass it, even if granted permissions within IAM.
- Ensuring Proper Access Controls: SCPs should be reviewed when implementing Delegated Administrator to avoid inadvertently restricting necessary actions.
- Logging & Monitoring: Ensure CloudTrail and AWS Config are enabled in the delegated administrator account to track activity and detect anomalies.
Best Practices for Secure Use of Delegated Administrator
- Follow Least Privilege Principle
- Grant only necessary permissions for the delegated administrator account.
- Use SCPs to Restrict Risky Actions
- Example: Prevent the delegated administrator from modifying organization-wide security settings.
- Enable Logging & Monitoring
- Use AWS CloudTrail, AWS Config, and Amazon GuardDuty to monitor changes and detect anomalies.
- Regularly Review Delegated Permissions
- Audit IAM roles and policies within the delegated account to prevent privilege creep.
- Limit Delegation to Trusted Accounts Only
- Do not delegate administrative privileges to accounts with broad access to external services or lower security postures.
- Test SCPs Before Deployment
- Ensure SCPs do not inadvertently block necessary actions for the delegated administrator.
Conclusion
Delegated Administrator in AWS Organizations is a powerful feature that improves security, operational efficiency, and compliance by reducing reliance on the management account. However, it must be carefully implemented to avoid misconfigurations, unnecessary privilege escalation, and security gaps.
By following best practices such as least privilege access, SCP enforcement, logging, and regular audits, organizations can leverage Delegated Administrator securely while maintaining strong governance across AWS accounts.
ZEST for Cloud Risk Resolution
ZEST helps organizations remediate and mitigate security risks including cloud misconfigurations and vulnerabilities. The platform automatically builds resolution paths that offer high-impact, low-effort solutions that enable security teams to slash their backlog and keep their risk exposure under control.
To see how security teams are benefitting, reach out to our team to schedule a demo.