Publicly disclosed computer vulnerabilities are organized into a globally recognized list called Common Vulnerabilities and Exposures (CVE). To determine their severity, a scoring system is applied, with the most widely used system being the Common Vulnerability Scoring System (CVSS), which is now in its fourth version.
While CVSS has been instrumental in standardizing vulnerability severity, it mainly focuses on the vulnerability’s inherent properties. Although CVSS does have exploitability components, it is often misused due to reliance on base scores alone. This means organizations often treat similarly scored CVEs as equal, regardless of their real-world risk.
This blog explores the Exploit Prediction Scoring System (EPSS), the Known Exploited Vulnerabilities (KEV) catalog, and the growing need for cloud-specific frameworks to prioritize vulnerabilities effectively.
The Exploit Prediction Scoring System (EPSS)
EPSS is designed to estimate the probability of a vulnerability being exploited in the next 30 days. Managed by the Forum of Incident Response and Security Teams (FIRST), EPSS complements CVSS by focusing on the real-world likelihood of exploitation. It uses a machine learning model trained on vast datasets, including:
- CVE details (e.g., vendor, age, Common Weakness Enumeration)
- Exploitation attempts observed in the wild
- Data from honeypots, threat intelligence reports, and government catalogs like CISA’s KEV
- Publicly available exploit code (Exploit-DB, GitHub, MetaSploit)
- Offensive security tools and scanners: Intrigue, sn1per, jaeles, nuclei
Why EPSS Matters
Traditional CVSS-based remediation strategies often lack critical context. For example, a vulnerability with a CVSS score of 7+ (high/critical) may never actually be exploited. EPSS, on the other hand, introduces a data-driven approach to prioritize patching, focusing on vulnerabilities most likely to introduce risk and impact your environment.
Key benefits of EPSS:
- Daily updates for real-time prioritization
- Probability-based scores that reflect exploitation likelihood
- Enables security teams to prioritize vulnerabilities that pose the most risk to the business
EPSS in Action
Take these examples:
1. CVE-2021-44228 (Log4j)
- CVSS: 10
- EPSS: 0.974 (97% likelihood of exploitation)
- Action: Prioritize immediately
2. CVE-2023-48795 (OpenSSH)
- CVSS: 5.9
- EPSS: 0.95 (95% likelihood of exploitation)
- Action: Medium CVSS but significant exploitation risk—address quickly
3. CVE-2024-3094 (XZ)
- CVSS: 10
- EPSS: 0.30 (30% likelihood of exploitation)
- Action: Deprioritize; focus resources elsewhere
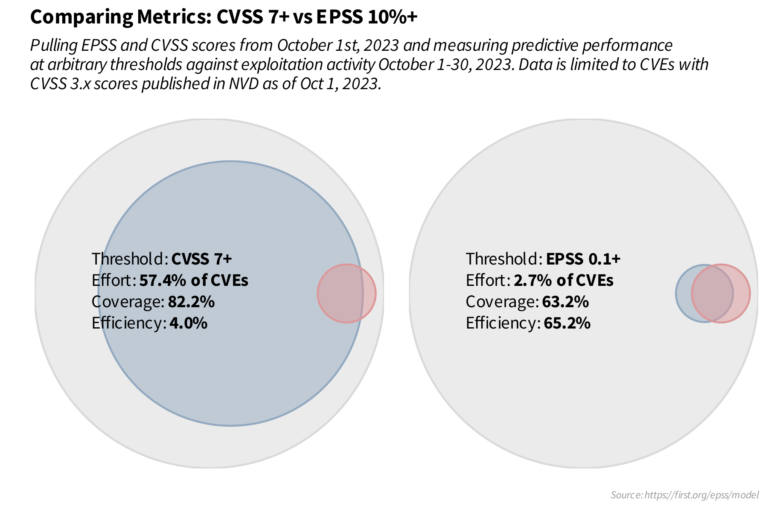
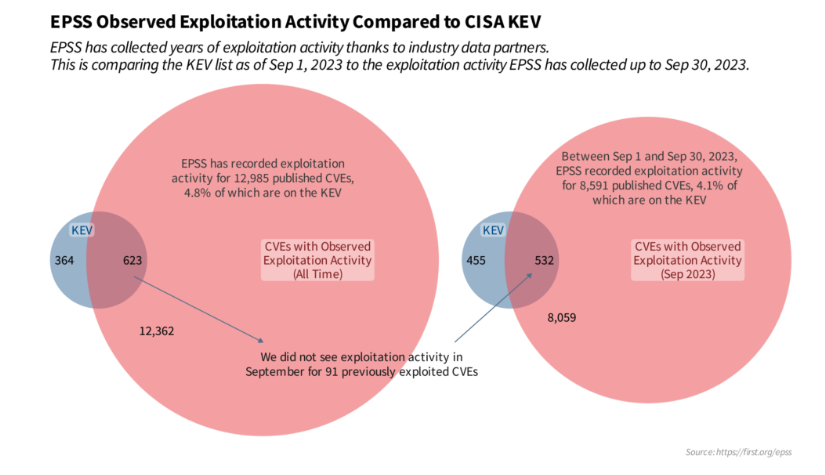
The Known Exploited Vulnerabilities (KEV) Catalog
The KEV catalog, maintained by the Cybersecurity and Infrastructure Security Agency (CISA), provides a curated list of vulnerabilities that are known to have been exploited in real-world attacks. Unlike CVSS or EPSS, KEV is binary, either a vulnerability has been exploited or it hasn’t.
Why KEV Is Important
KEV offers a direct and reliable way to identify vulnerabilities that demand immediate attention. By combining KEV with EPSS, security teams can:
- Validate EPSS predictions with confirmed exploitation data
- Identify actively exploited vulnerabilities in their environments
- Achieve a balance between proactive (EPSS-driven) and reactive (KEV-driven) patching strategies
For example, if a CVE appears in KEV and has a high EPSS score, it signals a critical vulnerability that requires immediate remediation. Conversely, a low EPSS score for a KEV-listed CVE might indicate specific exploitation scenarios, allowing tailored prioritization.
Do We Need a Cloud-Specific Framework?
While EPSS and KEV offer incredible insights for prioritizing vulnerabilities, cloud-native environments bring unique challenges that demand a new approach:
- Dynamic Attack Surfaces: Cloud environments are highly dynamic, with ephemeral workloads, containers, and serverless functions.
- Shared Responsibility: Cloud providers manage certain aspects of security, leaving customers responsible for others. Understanding this split is crucial for accurate prioritization.
- Contextual Relevance: Factors like the blast radius of an exploited vulnerability in a multi-tenant architecture or its impact on compliance should influence prioritization.
This raises the question: should we develop a cloud-specific framework for vulnerability prioritization, similar to EPSS or KEV? Such a framework could integrate:
- Cloud provider telemetry for real-time risk analysis
- APIs for automatic mapping of vulnerabilities to cloud resources
- A scoring model that accounts for shared responsibility, privilege escalation paths, and environmental context
Conclusion
The sheer volume of risks that surface on a daily basis means security teams are constantly battling an ever-growing risk backlog, making prioritization a critical component of any risk remediation program. EPSS and KEV have revolutionized the way we approach vulnerability prioritization, addressing critical gaps in traditional CVSS-based systems. However, as cloud adoption continues to rise, a tailored framework for cloud-native environments could be the next frontier in vulnerability prioritization.
If your interested in learning how ZEST helps enterprises streamline prioritization and expedite resolution of vulnerabilities, misconfigurations and other cloud risks, contact our team to see a demo.


.svg)